12 Days of Integrations — Yubico

It’s that time of year again… The leaves have fallen from the trees, every department store is playing “All I Want for Christmas is You” on a loop, and I can finally justify wearing that hand-knit beanie I bought on Etsy (even though I live in California).
To celebrate, Sentry is highlighting twelve of our many integrations with an ornament hung with care each day on our festive Sen-Tree. We hope you return every day to enjoy these GIFs with your holiday feast, egg nog, Manischewitz, or pour-over artisan coffee.
Our first featured integration is Yubico.
We think security is important. You think security is important. Our parents think security is important. Rarely do such a wide range of people agree so strongly on one thing. That’s why Sentry adheres to certification and compliance standards like HIPAA / HITECH, PCI DSS, and Privacy Shield (among others). It’s also why we introduced two-factor authentication (2FA) for all accounts two summers ago. Ah, remember summer, when it was so warm? Nice.
When using 2FA with Sentry, there are several options available for your second factor: SMS, Google Authenticator (or a similar app that supports TOTP), or a U2F device like Yubico’s appropriately-named YubiKeys.
If you’re not already familiar, YubiKeys are small USB sticks that act as physical authentication devices. If the YubiKey is plugged into your computer, then Sentry (and the many other apps that support YubiKeys) can authenticate — with the push of a (physical) button — that you are who you say you are and allow you to log in. If it’s not plugged in, then you won’t be authenticated and you can’t log in. Simple as that. There is probably no more direct way to protect yourself from malware, phishing, and man-in-the-middle attacks. It’s pretty difficult for someone to get in the middle of you and a USB port.
Different services use different types of security protocols. YubiKeys are capable of performing multiple protocols, so you can use the same key for almost an unlimited number of services. They support FIDO U2F, Secure Static Passwords, smart card (PIV), Yubico OTP, Code Signing, OpenPGP, OATH-TOTP, OATH-HOTP, and Challenge-Response.
YubiKeys integrate easily with Sentry right out of the box, with Yubico providing a hosted validation service, open-source server software, and native integration with hundreds of other apps. They also provide USB-C versions of their keys, making this one of only roughly four things that don’t require an adaptor to work with newer MacBook Pros.
How does it work?
First, you’ll need a YubiKey. Then you’ll need to activate 2FA in your account. To do so, go to account settings, click the button to enable two-factor authentication, and select the U2F hardware option from the list that follows. Then plug in your YubiKey to enroll it.
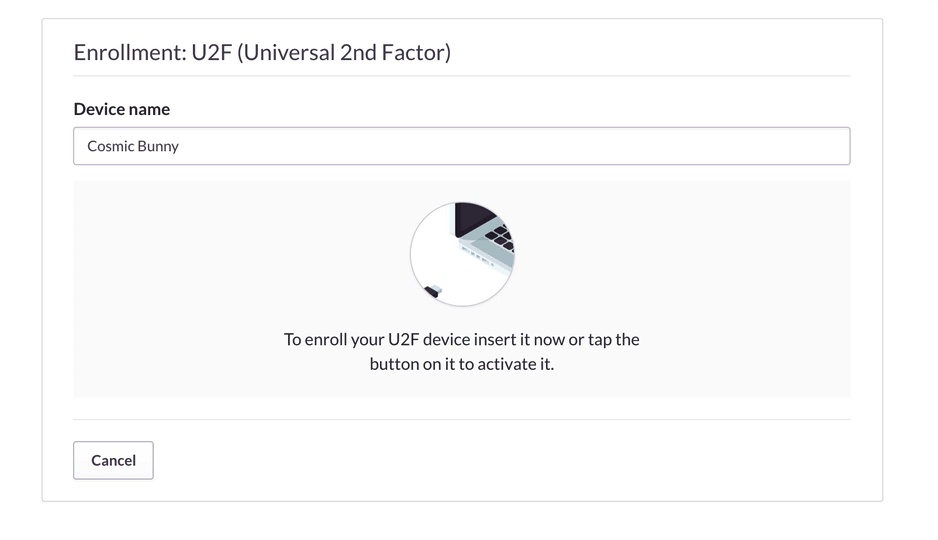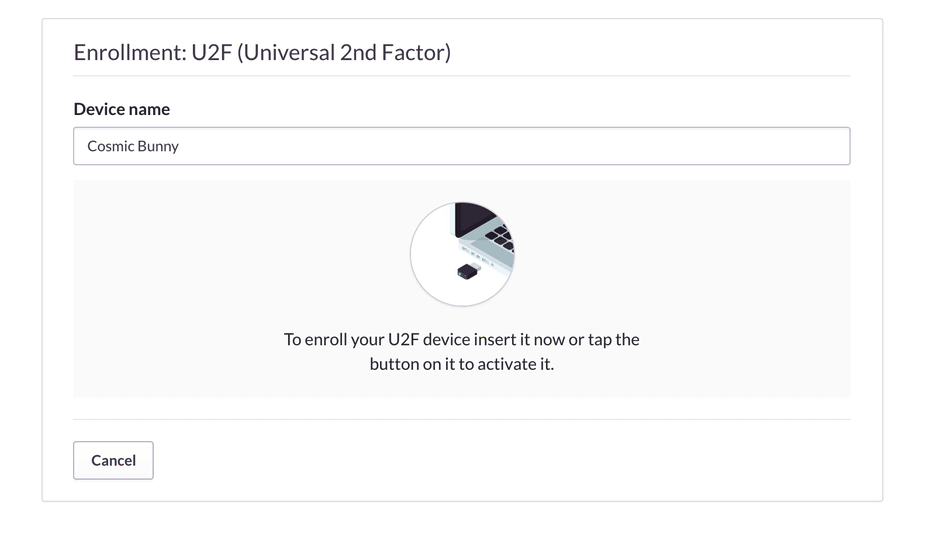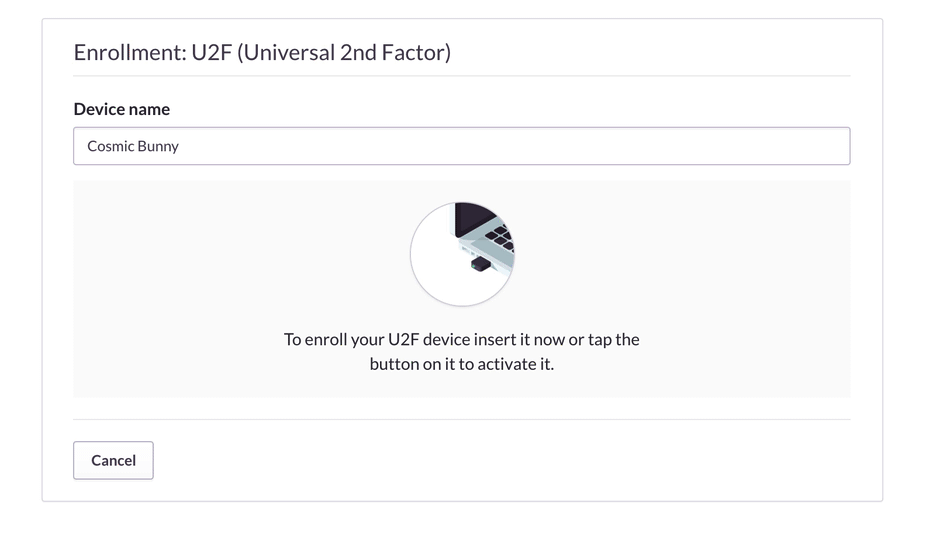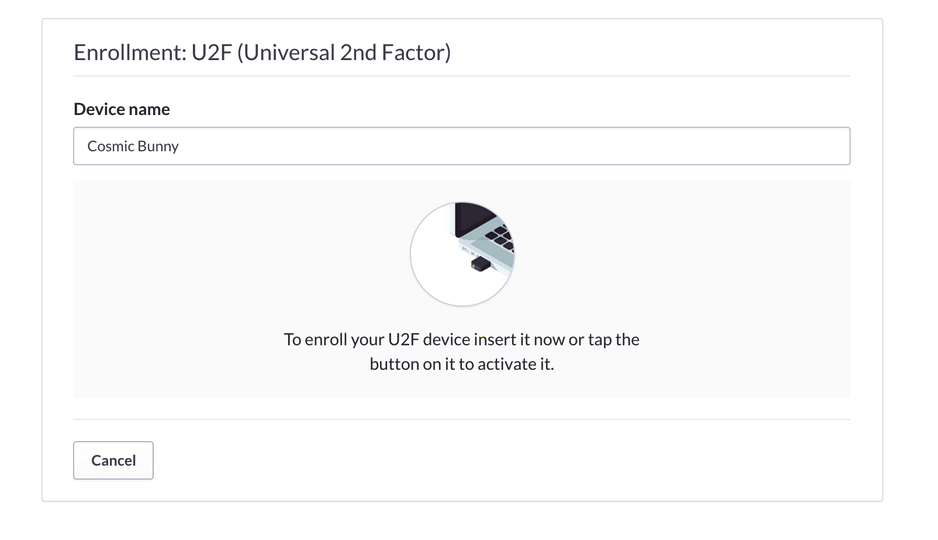
Enabling 2FA
All done! Now, any time you log in to Sentry, you’ll be prompted to plug in your YubiKey (unless it’s already plugged in).
Also, if you like deals, until Friday, you can get a second FIDO U2F Security Key free from Yubico when you purchase one with this special Sentry promo code:
That’s what is traditionally known as a buy-one-get-one (BOGO) deal. But you and I both know that it’s actually a buy-one-get-two deal. Go tell the world!
Disclaimer section (say this really fast while reading it quietly to yourself):
Deal valid with FIDO U2F Security Keys only. Limit one coupon per customer. Discount cannot be combined with other Yubico offers. Coupon valid at yubico.com. Not for resale. Deal expires on December 8, 2017 at 11:59pm PT.