Freeze Bad Deployments in their Tracks with the GitHub Deployment Gate Integration
If you have a large codebase with multiple developers shipping quickly – errors need to be caught quickly as well. To help ensure your code is performant and reliable while you’re deploying code, we partnered with GitHub to build a bridge between your CI/CD workflow and your favorite error monitoring tool (Sentry, of course). Sentry helps you detect new issues after a release - and with the Deployment Gate integration with GitHub, you can now use Sentry's monitoring insights in your deployment pipelines to automatically spot errors and revert bad rollouts.
Previously, developers using GitHub could only use the built-in environment protection rules to require a manual approval, delay a job, or restrict the environment to certain branches. There was no support for developers to create and implement custom rules that can be configured within their deployment workflows to safely promote deployments to production environments.
Now, Github Enterprise Cloud and Enterprise Server customers have an extensible way to create their own rules to control deployment workflows through Deployment Protection Rules. By configuring these rules, you can set up quality gates on every deployment environment, stopping deployment that do not meet specific quality criteria.
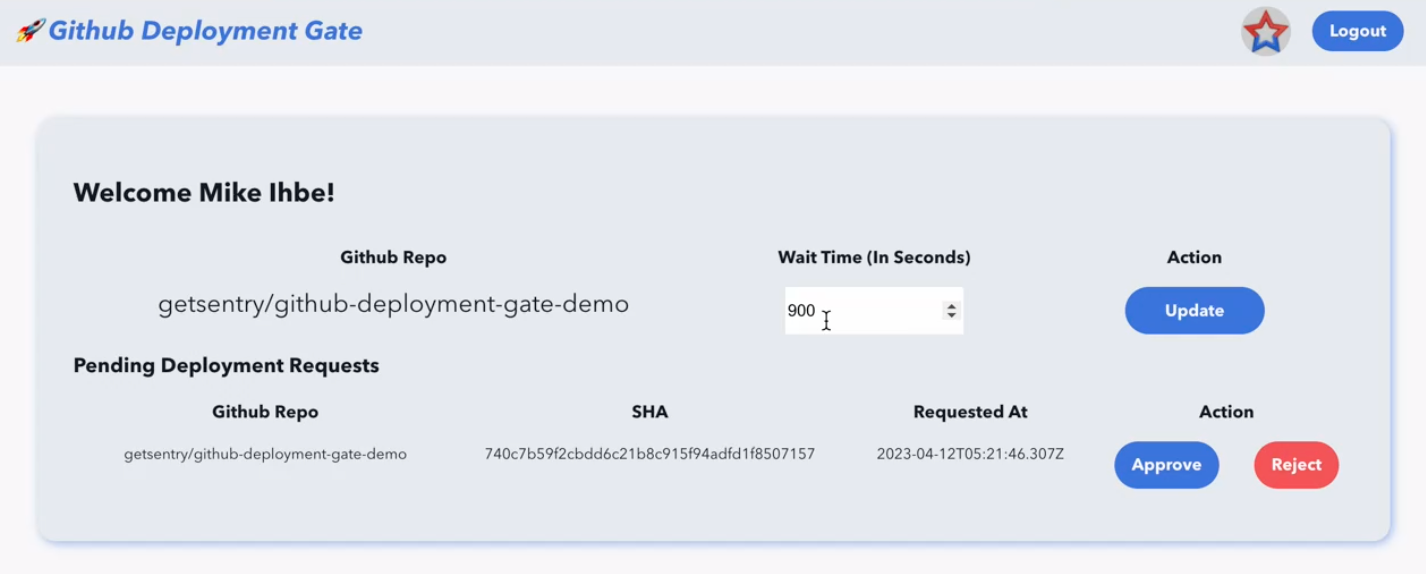
With the Sentry GitHub Deployment Gate integration installed, you can set up a rule that will block a rollout from continuing in GitHub if a new issue is detected by Sentry in the release. Depending on how your pipeline is written, you can either prevent the rollout from expanding if an error is detected, or revert the deployment altogether. This capability can be especially helpful during a canary release when you’re scaling up a rollout and need to immediately roll back the release if anything breaks. If there are new issues, the gate will be rejected. If there are no issues, the gate will be approved and the rollout will continue. In Sentry, you can look at the ‘new issues count’ for a release within a project. (If there are any within the configured time window, the gate will automatically be rejected.)
How to get started
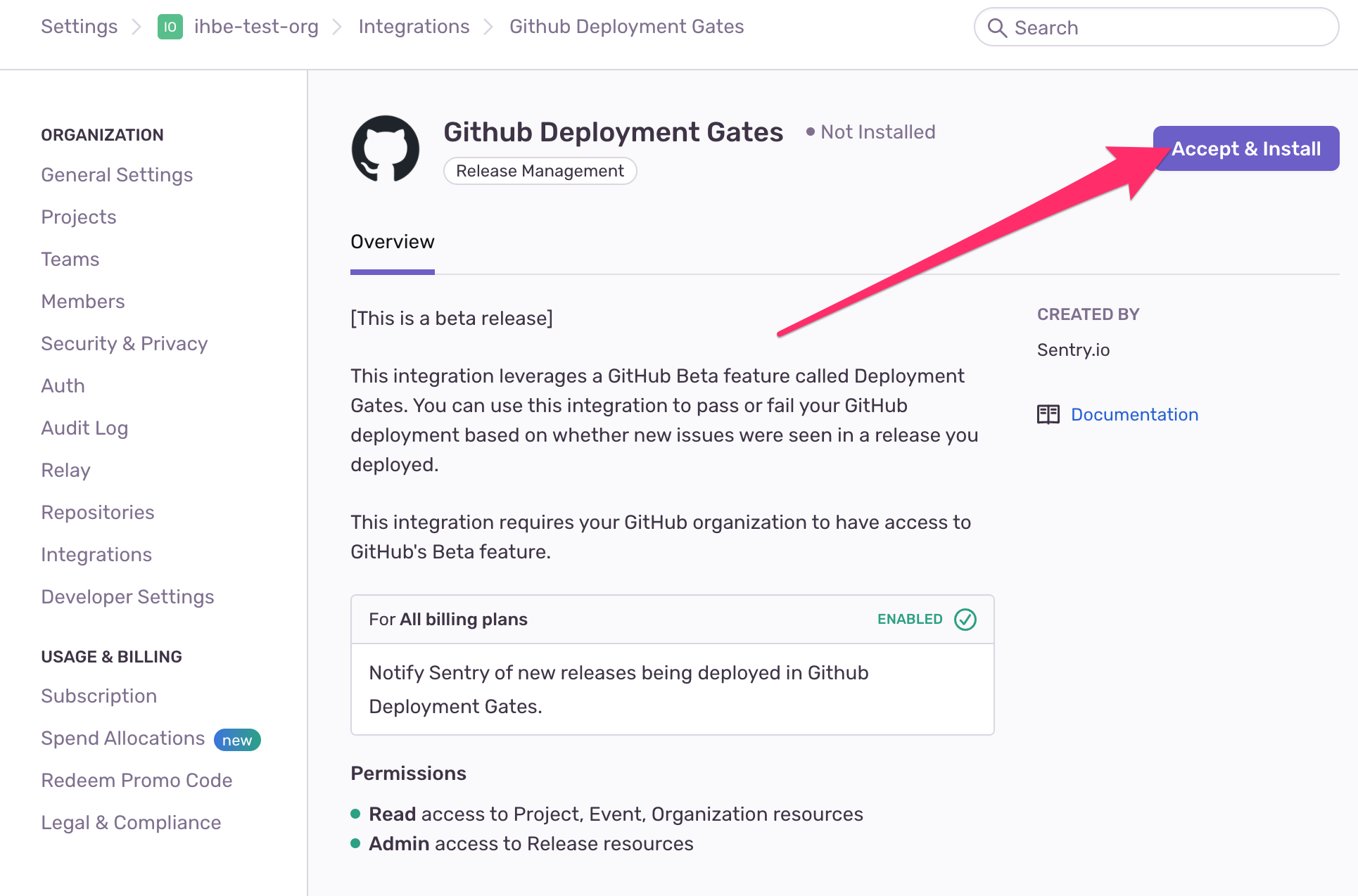
First, head to your Sentry organization settings and click on "Integrations".
Search for the “GitHub Deployment Gates” integration.
Agree to the terms, accept and install the integration.
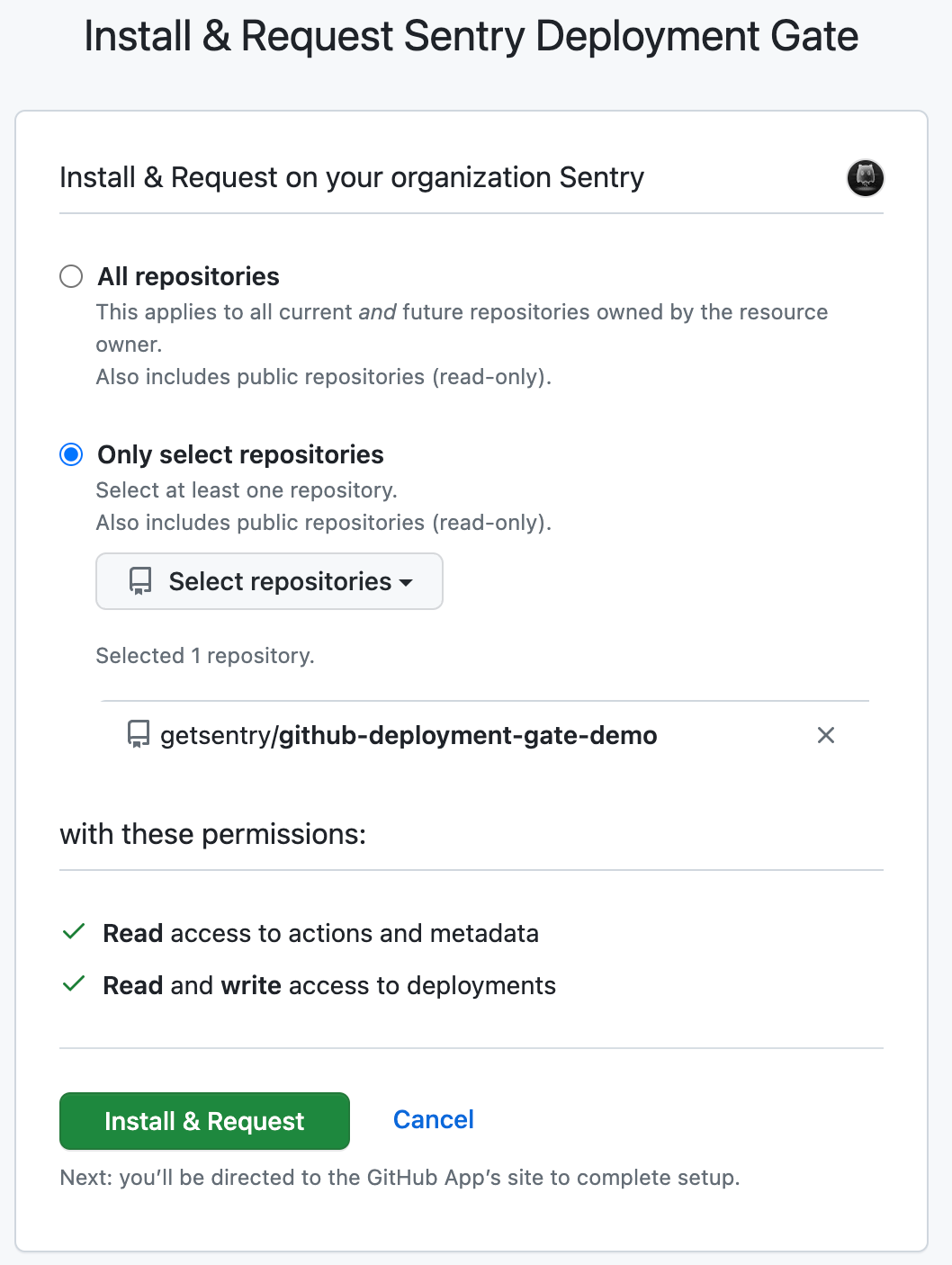
Sign in to GitHub and install the "Sentry Deployment Gate" application.
Select the repositories to enable.
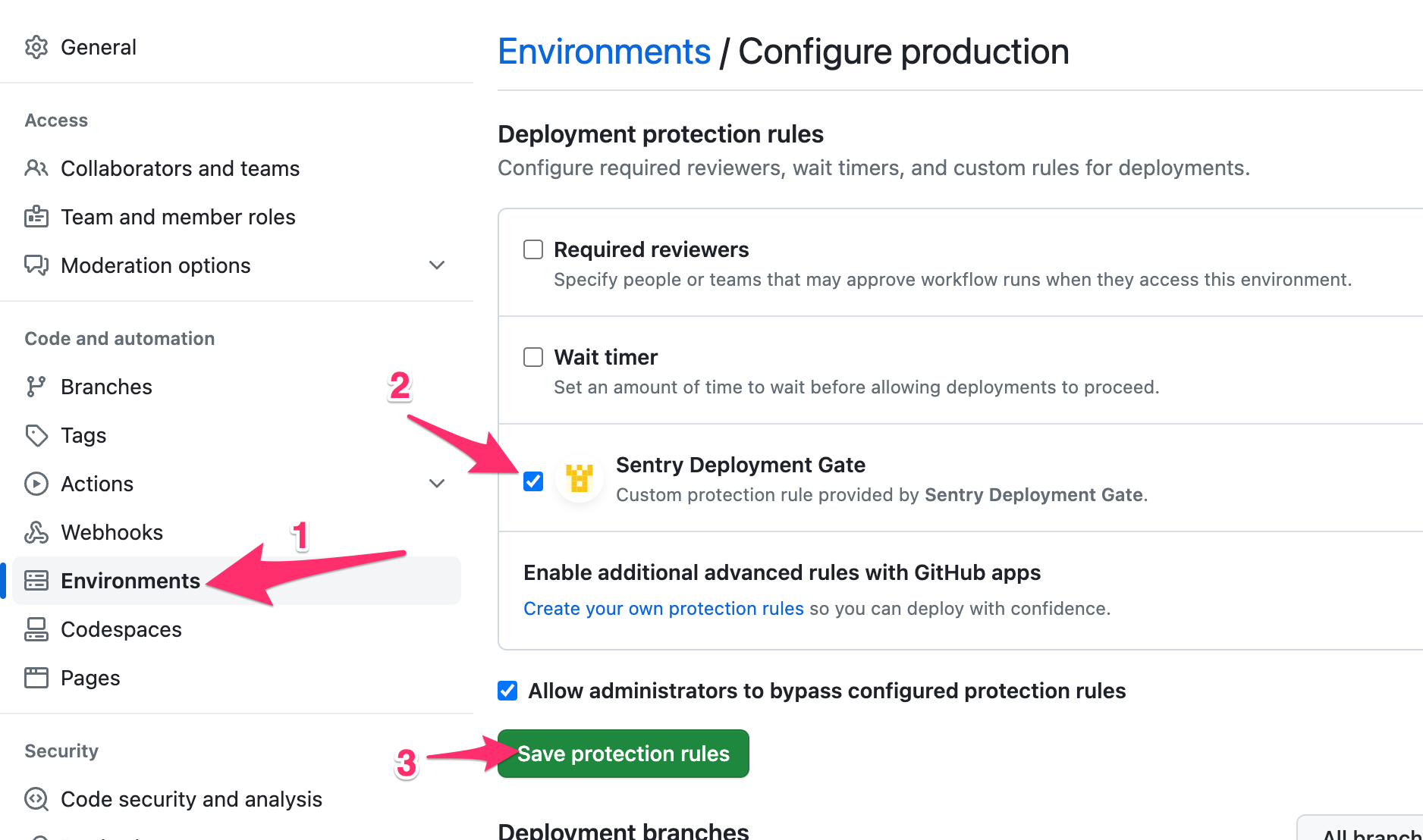
From your repository settings, click on "Environments" in the left-nav. Select the environment to configure. Turn on the protection rule for this application, then save the settings.
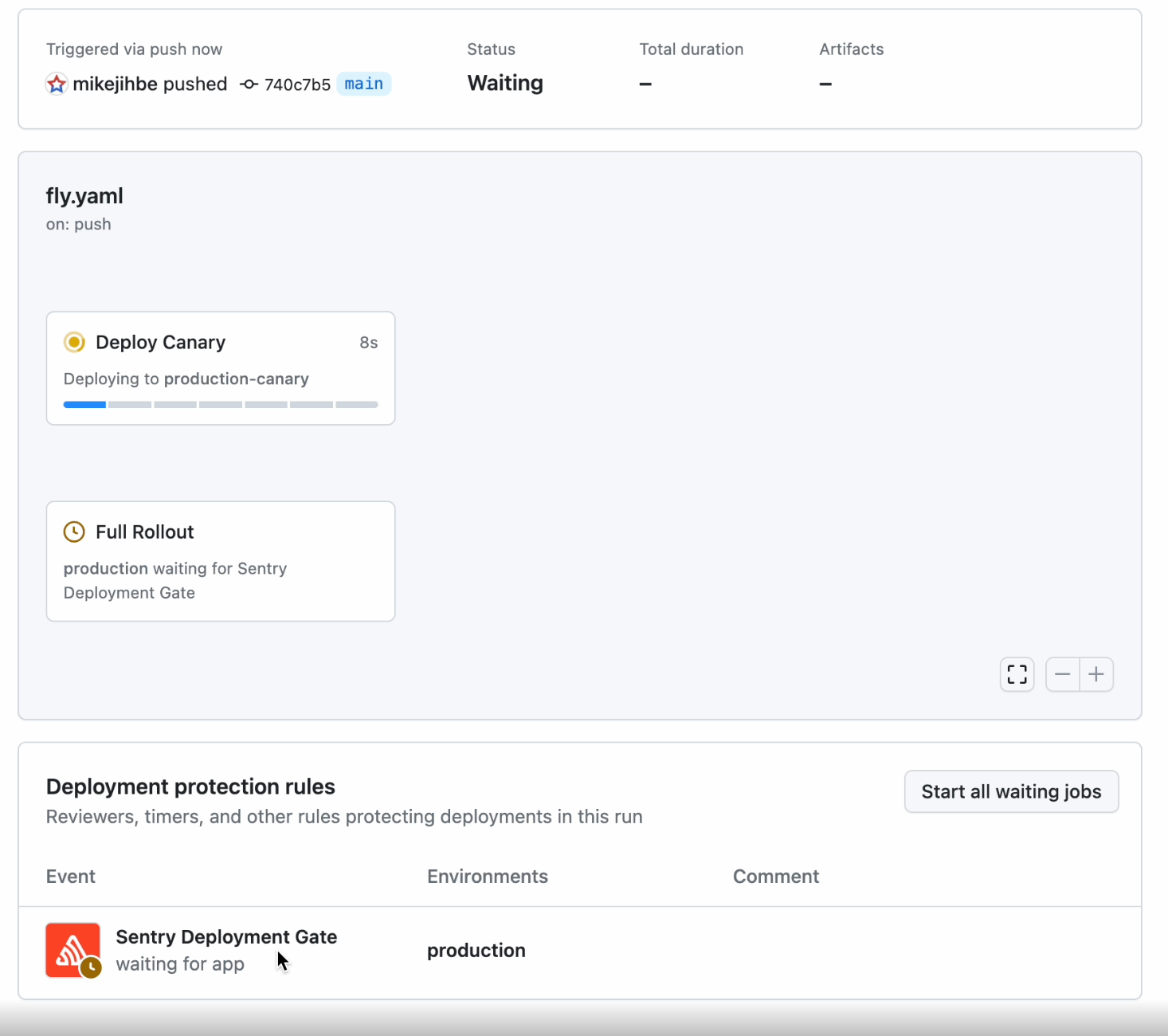
From here, you can trigger a new deployment. When you push this out to the repository, it will trigger the GitHub deployment workflow.
You can also configure the wait time to see if there are new errors before continuing the deployment.
For more information on how to get started and how it works, check out this demo application.
By integrating deployment rules with Sentry, you can stop worrying about reliability of your release process and ensure that only high-quality, thoroughly tested code reaches production. The result? Better overall development lifecycle with fewer bugs, better testing, and more reliable code.
Interested in learning more or have product feedback? Drop us a line on GitHub, Twitter, or Discord. And if you’re new to Sentry, you can try it for free or request a demo to get started.