Notice of (Internet) Address Change
Notice of (Internet) Address ChangeAs part of continuing projects to increase the reliability of sentry.io,
the IP addresses associated with the service will be changing soon.
These changes may require customer-side updates to firewall rules to
continue uninterrupted service.
Specifically, firewall rules that restrict traffic based on IP addresses
will have to be changed for the following circumstances:
Firewalls between an application monitored by Sentry and the Sentry
service (sentry.io)Firewalls between Sentry’s service and:
web servers or CDNs that serve JavaScript source and/or source map
filesservers configured to receive webhook HTTP requests
If neither of these apply, no changes are needed. We hope you continue
to use and enjoy Sentry!
We plan to migrate all traffic to the addresses below, starting on June
21, 2017.
Inbound Address
35.188.42.15
When a Sentry client SDK transmits errors to sentry.io, DNS will return
the above IP address alongside the existing service addresses. If you
have previously configured network rules between your application
servers and the Internet to limit outbound requests, those rules will
need to be updated to add this new address.
Outbound Addresses
35.184.238.160
104.155.159.182
104.155.149.19
130.211.230.102
When configured by customers, sentry.io also sends web requests to its
customers’ servers. The most frequent requests Sentry makes are to fetch
JavaScript source files and source
maps, but we
also connect using webhooks and other integrations. If you have
configured network rules that only allow inbound requests from specific
addresses, you will need to update those rules to include the
additional addresses.
Alternative Methods of Authentication
In order to alleviate some of the pains caused with updating these
addresses, Sentry provides the ability to append a token to our outbound
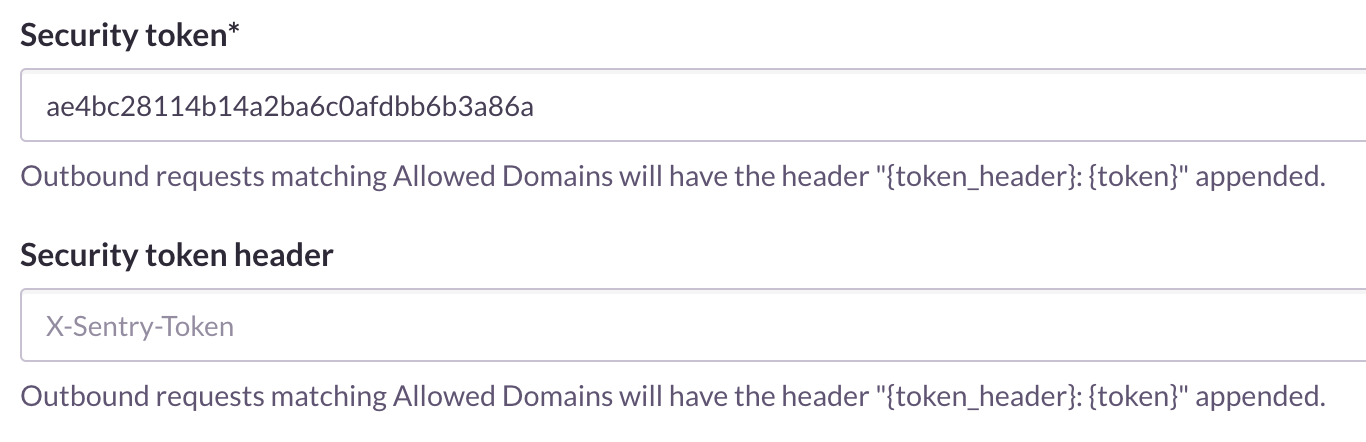
request headers. You may configure this token by going to your
Project Settings, and scrolling down to “Security Token” where you’ll
find the following form:
By default, all outbound requests are appended with the X-Sentry-Token
header using the security token as the value. This token can be verified
by a webserver or a proxy, denying all traffic that does not match.
Here’s an example for using nginx to deny unauthorized requests:
map $http_x_sentry_token $from_sentry {
f48e8f0eb1c911e493090025902d9efc 1;
default 0;
}
location / {
if ($from_sentry = '0') { return 403; }
}Note that both the header name and token value can be configured to suit
your preferences.
Moving forward, we strongly encourage your organization to use this
authentication method instead of IP whitelisting.