Deprecating TLS 1.0 and 1.1
Deprecating TLS 1.0 and 1.1
On November 1, Sentry will no longer be providing support for TLS 1.0 and 1.1 on https://sentry.io and https://o*.ingest.sentry.io.
Originally this blog post mentioned plans on deprecating https://sentry.io and https://app.getsentry.com as ingestion domains. We still have intentions to deprecate them, however, this will take longer time than expected. We have decided to reduce the scope to only deprecation of TLS 1.0/1.1 on November 1st.
TL;DR
This article will be of interest to you if you’re using Sentry SDKs on hardware platforms/OSes/libraries that are 5+ years old.
What is changing?
Deprecating TLS 1.0 and 1.1
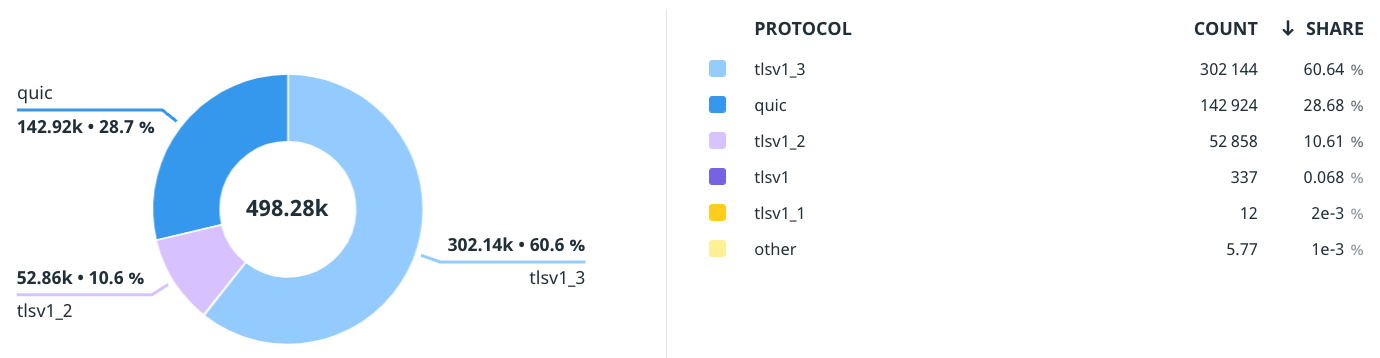
Why? Transport Layer Security (TLS) is the protocol at the heart of HTTPS. Its primary purpose is to encrypt the communication, thus preventing eavesdropping and data tampering. In the past, several security vulnerabilities in TLS have been found, the most famous ones being BEAST and POODLE. The solution has been to update with newer versions of TLS protocols that fixed those vulnerabilities and implemented other minor security improvements. Currently, TLS 1.2 and TLS 1.3 are supported by all major browsers and modern software due to these improvements.
For historical reasons, Sentry continued to support all TLS versions starting from 1.0. But now, the time has come to retire TLS 1.0 and 1.1.
Fortunately, according to our stats, less than 0.1% of requests to Sentry are using TLS 1.0 or 1.1.
We understand that it might not be possible to switch to newer TLS versions in some situations, like older devices, legacy systems, etc. For such cases, we provide separate endpoints with TLS 1.0 and 1.1 enabled. To use them, you will need to update your Sentry SDK settings with these endpoints:
https://o*.insecure.sentry.io– for event ingestionhttps://insecure.sentry.io– for API calls
We are going to keep these “insecure” endpoints for at least 1 year.
Timeline
TLS 1.0 and 1.1 will be permanently disabled on November 1. We want to ensure the most seamless transition for Sentry customers so we’re taking these extra steps.
August 22: Publication of this blog post.
https://o*.insecure.sentry.io and https://insecure.sentry.io are already publicly available.
October 3 till November 1: Series of brownouts. Throughout October, we are going to temporarily disable TLS 1.0 and 1.1 for a few hours on each weekday. The purpose is to provide Sentry customers a warning and allow some time to make corresponding changes to SDKs, etc. Keep an eye on our StatusPage for exact dates.
https://o*.ingest.sentry.io– TLS 1.0/1.1 connections will failhttps://sentry.ioandhttps://app.getsentry.com– TLS 1.0/1.1 connections will fail
November 1: TLS 1.0 and 1.1 will be disabled on sentry.io and o*.ingest.sentry.io.
We’ll be updating this blog post with relevant information as we move ahead in the timeline, so please check back if you believe this affects you.